Work on Porter with us!
We are actively seeking out new contributors with the hopes of building up both casual contributors and enticing some of you into becoming reviewers and maintainers.
Learn how to Join Us!
Take everything you need to do a deployment, the application itself and the entire process to deploy it: command-line tools, configuration files, secrets, and bash scripts to glue it all together. Package that into a versioned bundle distributed over standard Docker registries or plain tgz files.
Now anyone can install your application without deep knowledge of your deployment process, or following a step-by-step deployment doc, regardless of the tech stack.
Porter is never a replacement for an existing tool. Think of it as doing extra nice things on top of what those great tools already do! Below are some reasons why working with bundles with the tools embedded inside is helpful vs. using the same tools standalone.
Package everything you use to deploy in a single artifact that can be easily distributed over registries and across air gapped networks.
JIT secret injection, immutable artifacts, and container security are just some of Porter's security features.
Save time because the bundle contains the exact version of your deployment tools. Users don’t need to find and install tools or switch between versions.
View rich metadata about a deployment. Run porter explain to quickly see how to customize an installation with parameters, what credentials are needed by the bundle. There is no need for detailed installation documentation.
Reduce the operational knowledge required to manage an application. Often deployments involve multiple tools, such as terraform, helm, kubectl; all glued together with bash scripts. Bundles abstract away the details of a deployment, and provide a consistent set of commands to deploy any application.
Manage deployments securely as a team. Porter uses secure just-in-time credential injection and remembers the parameters last used to deploy. Teammates don’t need to hunt down the proper values themselves, or copy sensitive credentials into local environment variables or files. Secrets remain secure in a secret store such as Hashicorp Vault or Azure Key Vault.
"It used to take a day for the dev team to roll out one to two environments. We’ve gone from that to the ability to parallelize our deployment pipeline to target thousands of instances overnight at the push of a button. The potential cost savings are significant given the scale we're talking about."
Ken Priyadarshi: EY Global Chief Architect
EY Technology
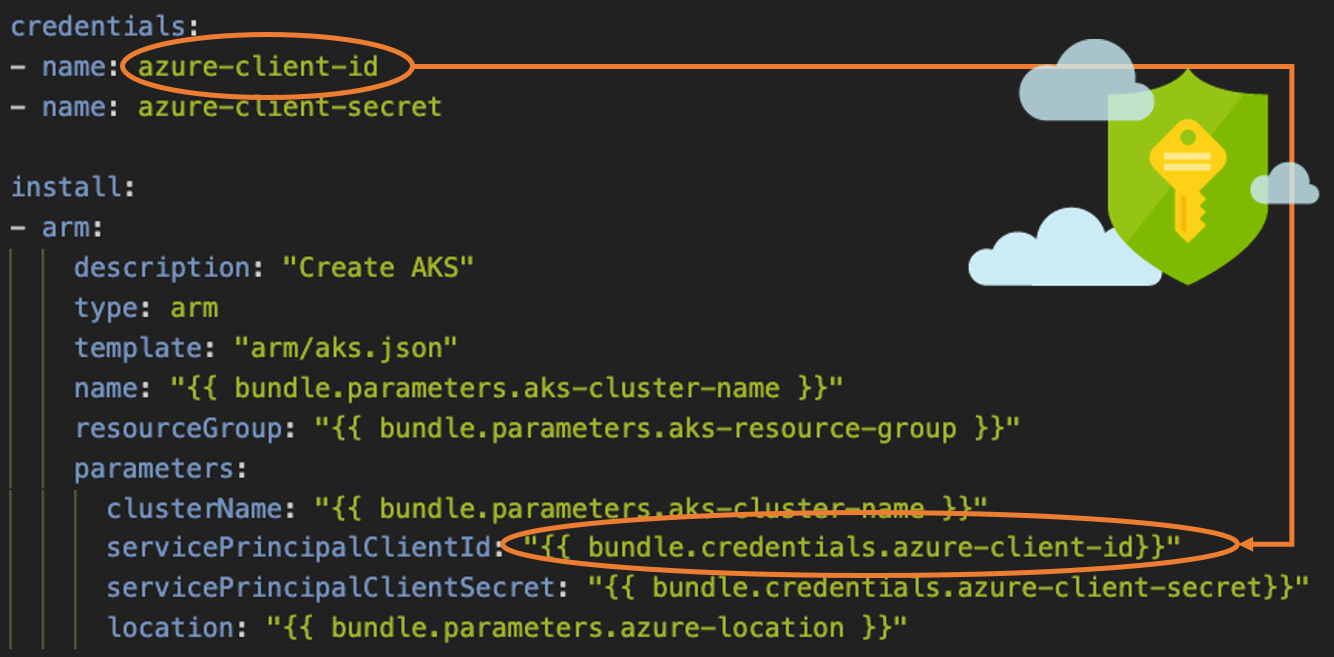
 Credentials and Secrets
Credentials and Secrets Credentials and secrets are retrieved from industry standard secret stores and securely injected.
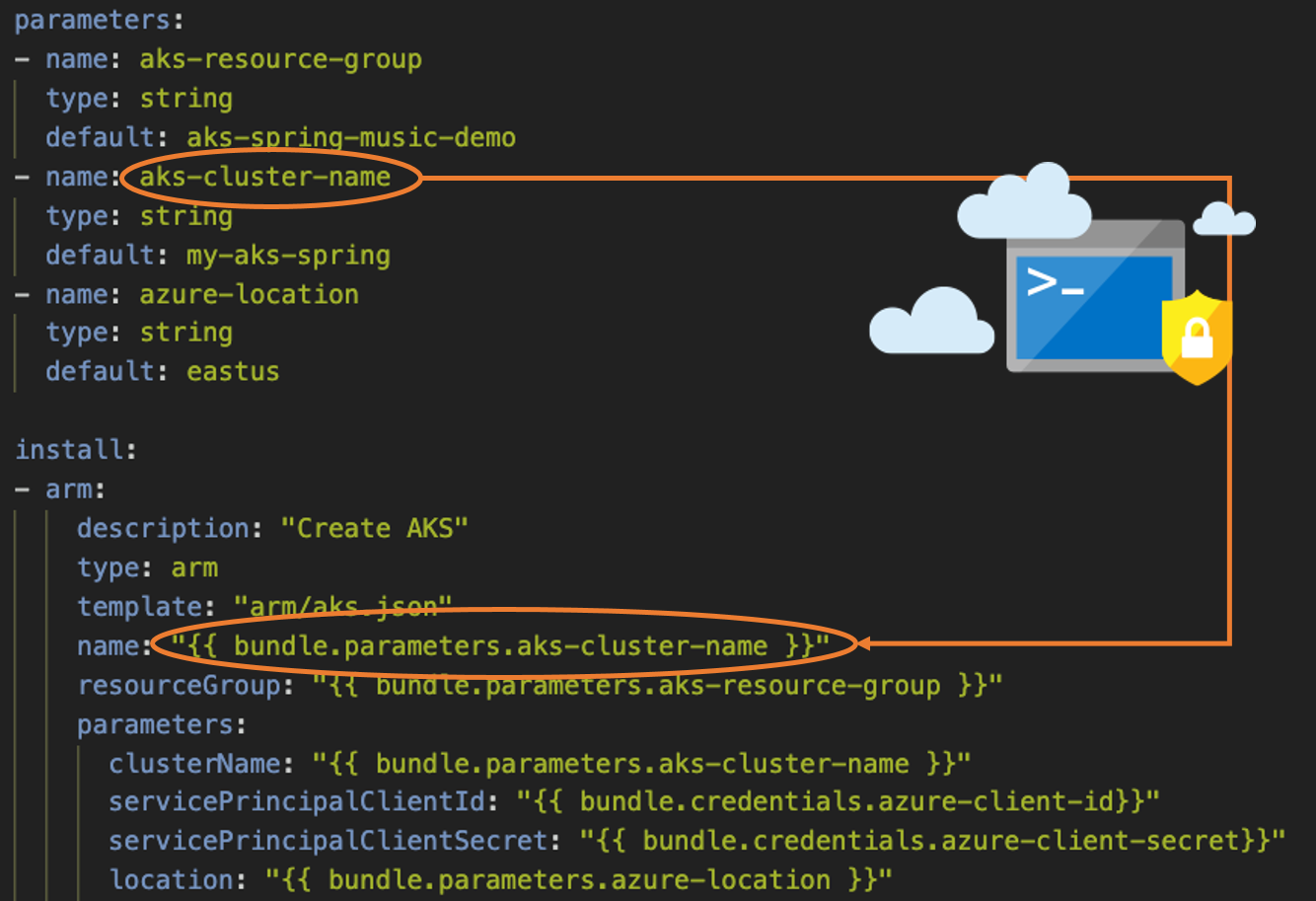
 Parameterized Bundles
Parameterized Bundles Use different configuration for production and staging, toggle feature switches and customize each installation of a bundle with parameters.
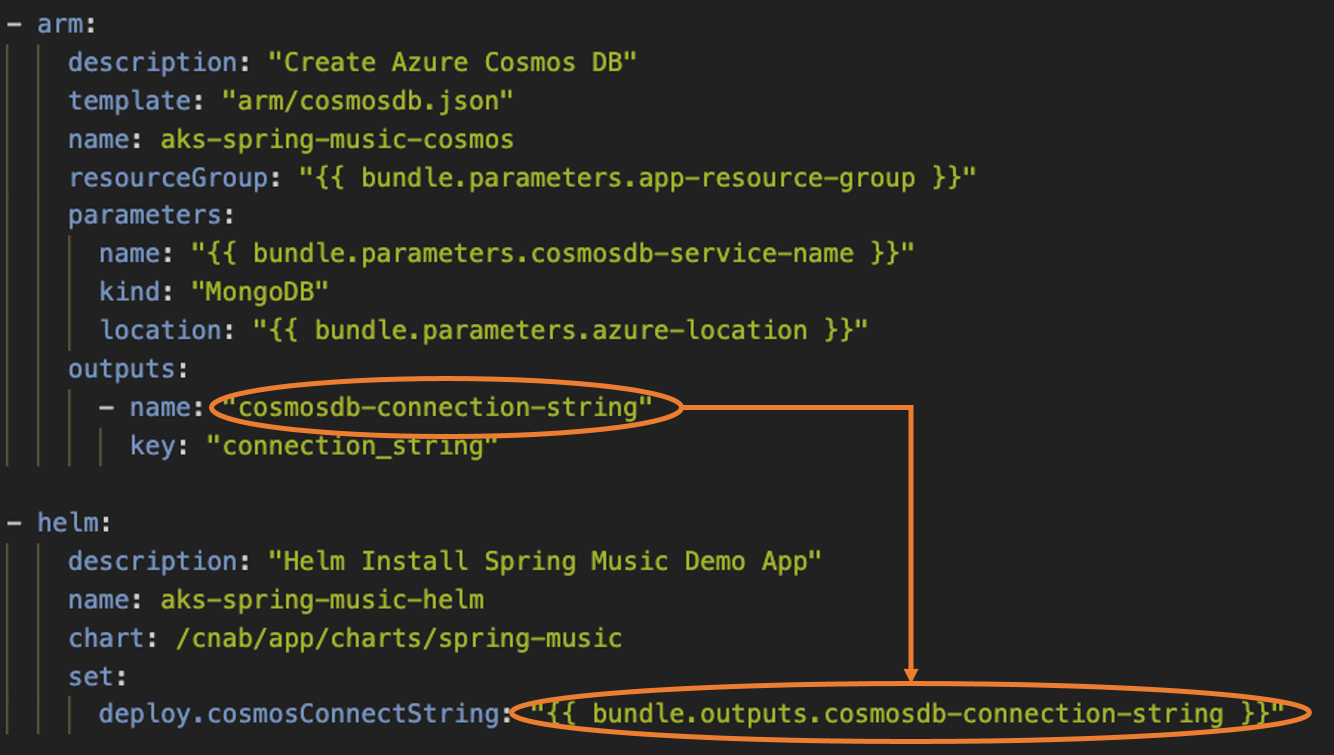
 Connect Action Inputs and Outputs
Connect Action Inputs and Outputs Wire together tools that were not designed to integrate and seamlessly pass data between them.
Porter is a cloud-agnostic tool that can work anywhere and with any tool, but in order to have great support for these clouds and tools, custom-made mixins are best.
Do you know tools we don't have Custom Mixins for yet?
More information about the Porter project, and how to contribute.